The Biggest Myth About Hacking
Many people imagine hackers sitting at keyboards guessing passwords one by one. In reality, most account takeovers don’t involve guessing at all.
Hackers already have millions — sometimes billions — of stolen usernames and passwords from past data breaches. Their job is simply to reuse them.
What Credential Stuffing Is (In Plain English)
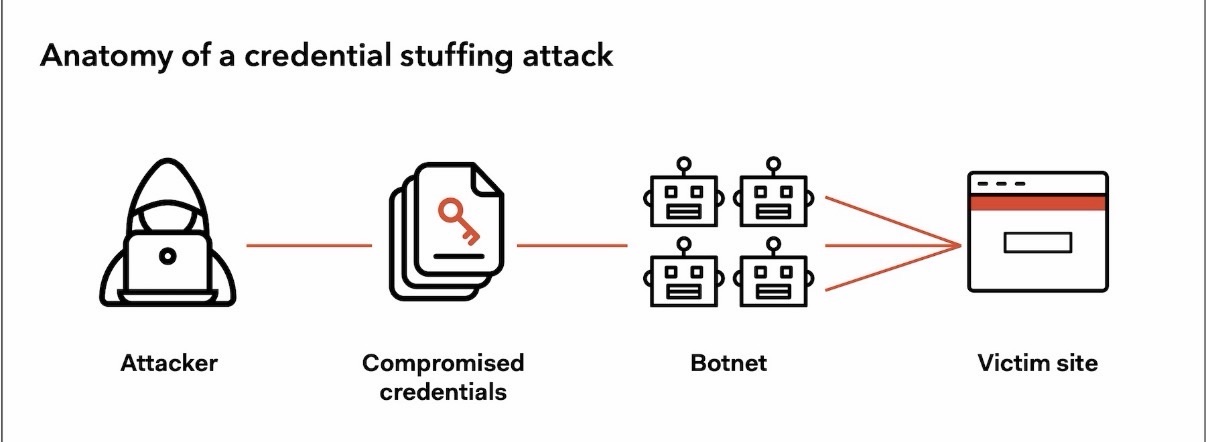
Credential stuffing is an automated attack where stolen login details are tested across thousands of websites and apps.
If you reused a password even once, attackers can:
Try it on email services Social media platforms Shopping sites Cloud storage Financial apps
All in minutes, using bots.
Why These Attacks Are So Effective
Credential stuffing works because:
Password reuse is extremely common Automation allows millions of attempts per hour Many sites still lack proper protections Users often don’t notice failed login attempts
Attackers don’t need skill — they need scale.
How Hackers Avoid Detection
Modern attackers use techniques such as:
Rotating IP addresses and proxies Mimicking normal user behavior Low-and-slow login attempts Targeting smaller or less-secure sites first
This makes attacks harder to detect and block.
What Happens After an Account Is Taken Over
Once access is gained, attackers may:
Change passwords and recovery emails Steal stored payment information Use the account to scam others Resell the account as “verified” Pivot to more valuable accounts
Email access often leads to total digital takeover.
Why Email Accounts Are the Real Target
Your email is the gateway to:
Password resets Financial accounts Social media profiles Cloud storage Personal and work data
That’s why attackers prioritize email accounts first.
How to Stop These Attacks Completely
The good news: credential stuffing is easy to block.
Best defenses:
Use unique passwords everywhere Enable multi-factor authentication (MFA) Monitor login alerts Change reused passwords immediately Secure your email account first
Even one of these steps dramatically reduces risk.
Final Takeaway
Hackers don’t need to crack your password — they just reuse one you already lost.
Account security today isn’t about being clever.
It’s about not giving attackers the same key twice.