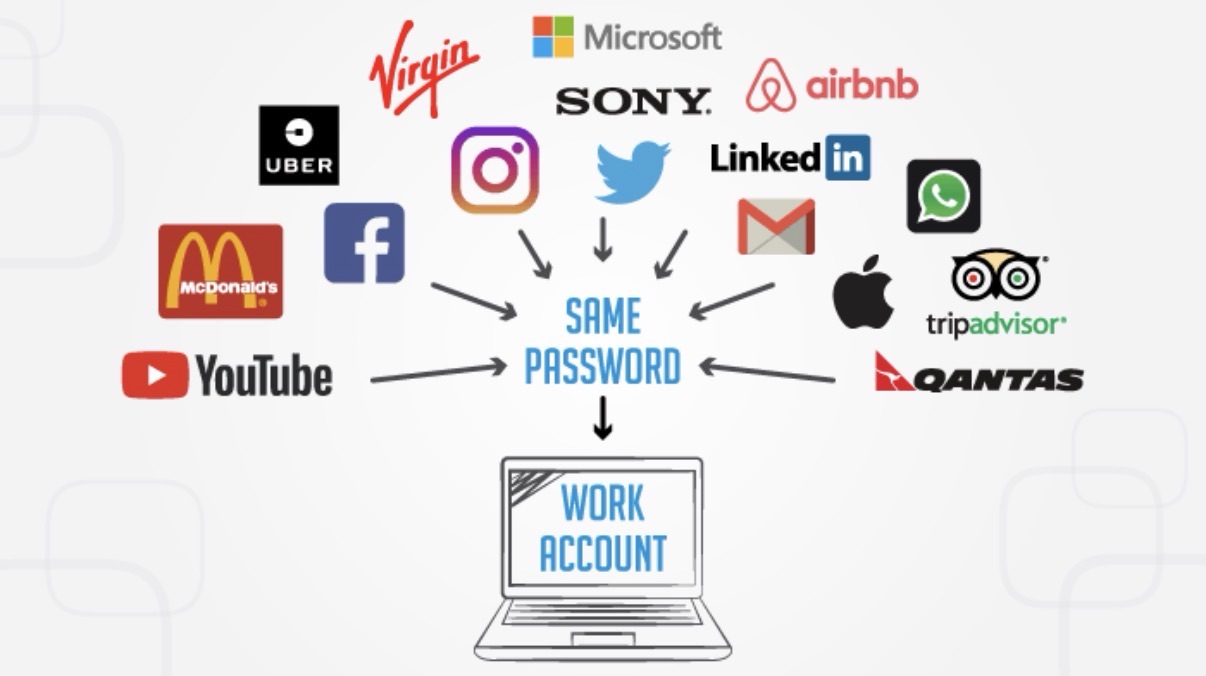
The Hidden Habit That Puts All Your Accounts at Risk
Reusing the same password across multiple websites is one of the most dangerous — and common — online habits. It feels convenient, easy to remember, and harmless. But in reality, password reuse turns one small security mistake into a full digital disaster. Hackers don’t need to break into every site you use — they only need one.
How Hackers Actually Exploit Password Reuse
When a website suffers a data breach, stolen email-and-password combinations are rarely used just once. Instead, attackers feed them into automated tools that try those same credentials across hundreds or thousands of popular platforms — email providers, social media, shopping sites, crypto wallets, and even banking portals.
This attack method is called credential stuffing, and it works frighteningly well because so many people reuse passwords. If one site falls, attackers can domino their way through your entire online life.
Why “Strong” Passwords Still Fail
Many people assume they’re safe because their password looks complex — a mix of numbers, symbols, and capital letters. But strength doesn’t matter if it’s reused.
If your “strong” password was leaked years ago in a breach you forgot about, attackers already have it. At that point, complexity is irrelevant — access is instant.
What Hackers Do After They Get In
Once attackers gain access to one account, they don’t stop there. Common next steps include:
Resetting passwords on other services using your email Locking you out by changing recovery details Stealing saved payment methods or personal data Impersonating you to scam friends or contacts Selling verified accounts on underground markets
In many cases, victims don’t realize what’s happening until multiple accounts are already compromised.
Why Password Reuse Is So Widespread
Despite years of warnings, password reuse is still common because:
People manage dozens of accounts Remembering unique passwords feels overwhelming Many underestimate how often breaches occur Older breaches feel “irrelevant” or forgotten
Unfortunately, attackers rely on these assumptions.
How to Break the Password Reuse Cycle (Without Stress)
You don’t need to memorize 100 passwords to stay safe. The most effective approach is also the simplest:
1. Use a password manager
It generates and stores unique passwords for every site — you only remember one master password.
2. Enable multi-factor authentication (MFA)
Even if a password leaks, MFA can stop attackers cold.
3. Change passwords tied to your email first
Your email is the master key to everything else. Secure it before anything else.
4. Assume old passwords are compromised
If you’ve reused a password for years, treat it as already exposed.
The Bottom Line
Password reuse is dangerous not because hackers are smart — but because it makes their job easy. One leak can turn into total account takeover in minutes.
The good news? This is one of the easiest cybersecurity problems to fix.
One habit change — unique passwords — can shut down an entire class of attacks.
The Hidden Habit That Puts All Your Accounts at Risk
Password reuse is one of the most common — and most dangerous — online habits. Reusing the same password across multiple websites may feel harmless, but it creates a single point of failure. When one site is breached, attackers can instantly access many others using the same login details.
This is why password reuse is the #1 reason accounts get hacked worldwide.
How Hackers Exploit Reused Passwords
When a website suffers a data breach, attackers collect leaked email-and-password combinations and test them across popular services like email providers, social media platforms, shopping accounts, and financial apps.
This automated process, known as credential stuffing, allows hackers to compromise thousands of accounts in minutes — without guessing a single password.
Why “Strong” Passwords Don’t Save You
Many people believe complex passwords are enough. But a strong password reused is still a weak password.
Once your credentials appear in any breach — even one from years ago — attackers can reuse them endlessly.
Password strength does not matter once the password is exposed.
What Happens After Hackers Get Access
Once attackers break into one account, they often:
Reset passwords on other services Take control of your email Steal stored payment methods Impersonate you to scam others Sell verified accounts on underground markets
Most victims don’t realize what’s happening until multiple accounts are compromised.
Why Password Reuse Is Still So Common
Password reuse persists because:
People manage too many accounts Remembering unique passwords feels overwhelming Old data breaches feel “irrelevant” The risk is underestimated
Attackers rely on these exact behaviors.
How to Stop Password Reuse (The Easy Way)
You don’t need to memorize dozens of passwords.
Best practices:
Use a password manager to generate unique passwords Enable multi-factor authentication (MFA) Secure your email account first Treat reused passwords as already compromised
These steps block the vast majority of real-world attacks.
Final Takeaway
Password reuse makes hacking easy. One leaked password can unlock your entire digital life.
The fix is simple, effective, and free: unique passwords everywhere.